Search
Search for projects by name
 Stargate v2 (LayerZero v2)
Stargate v2 (LayerZero v2)
L2BEAT Bridges is a work in progress. You might find incomplete research or inconsistent naming. Join our Discord to suggest improvements!
About
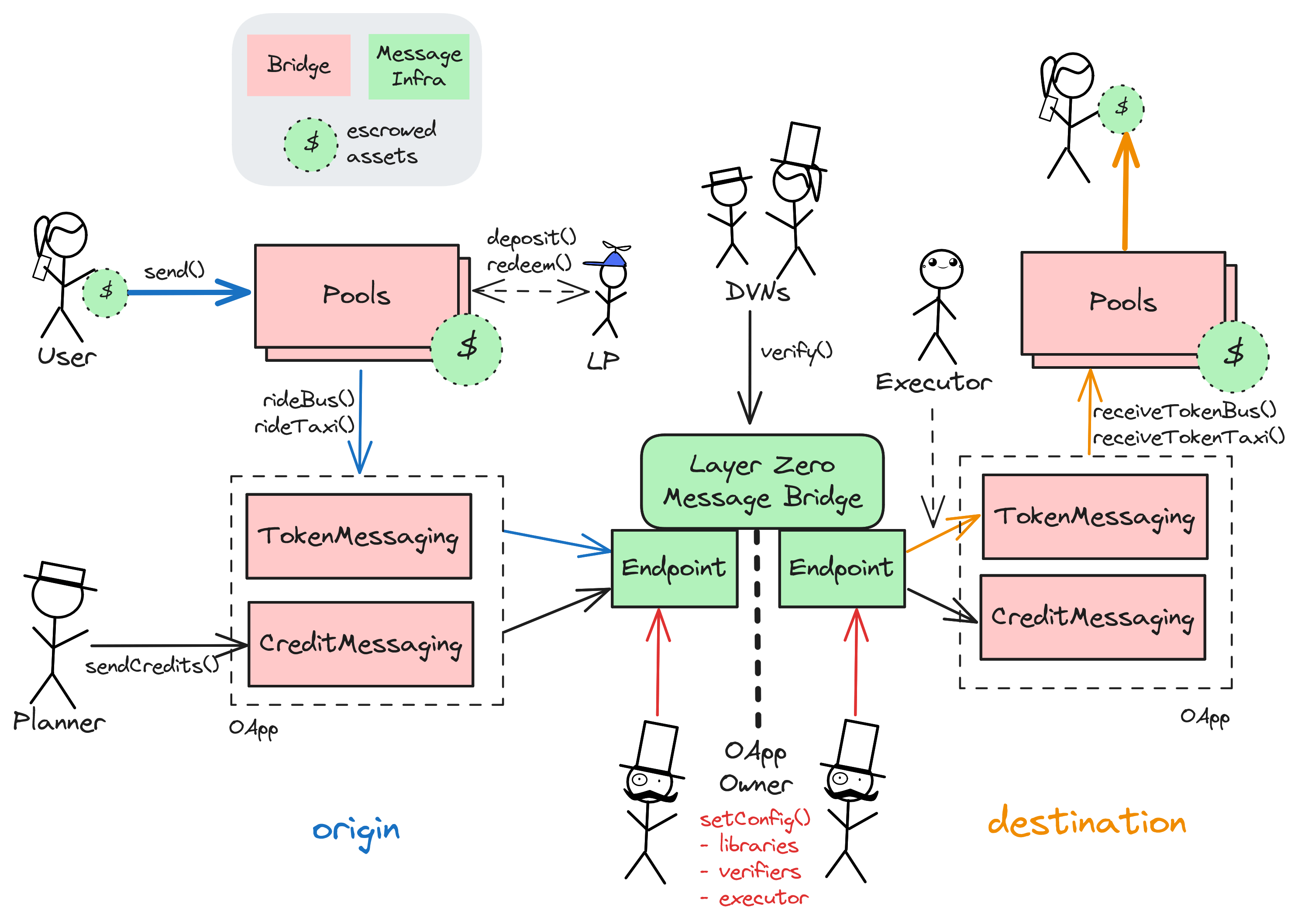
Stargate v2 is a Hybrid Bridge (mainly Liquidity Network) built on top of the LayerZero messaging protocol.
About
Stargate v2 is a Hybrid Bridge (mainly Liquidity Network) built on top of the LayerZero messaging protocol.
Stargate v2 is a Hybrid Bridge (mainly Liquidity Network) built on top of the LayerZero messaging protocol.
It uses liquidity pools on all supported chains, supports optional batching and a Token Bridge mode called Hydra that can mint tokens at the destination.
Funds can be stolen if
Funds can be frozen if
Users can be censored if
Principle of operation
On chains where assets are available through other bridges, Stargate acts as a Liquidity Bridge. This requires Stargate liquidity pools for assets at the sources and destinations since no assets can be burned or minted. While liquidity providers need to keep all pools buffered with assets, users can deposit into a pool on their chosen source chain and quickly receive the equivalent asset at the destination through an Executor. Users can choose between an economical batched bridge mode (‘bus’) or an individual fast ‘taxi’ mode that delivers the bridging message as soon as the user deposits.
While Stargate operates the local token pools on each supported chain, they are all connected through the LayerZero messaging protocol, which is responsible for verifying and delivering the crosschain messages. Verification is done by Stargate-selected permissioned verifiers (called DVNs in LayerZero terminology), currently configured as a 2/2 of Stargate and Nethermind custom Multisigs. Crosschain message passing is done by professional relayers and executors but could technically be done by anyone (even the user themselves if they have access to the bridge message signed by the two verifiers e.g. in case they have committed the verification onchain).
Just like the assets themselves, so-called credits (also OFTs) are bridged among the supported pools in the Stargate v2 system. Credits can be seen as claims on assets, so a liquidity pool needs credits for a remote pool to be able to bridge there. These credits can be moved and rebalanced (but not minted) by a permissioned role called Planner.
LayerZero messaging
The LayerZero message protocol is used: For validation of messages from Stargate over LayerZero, two DVNs are currently configured: Nethermind and Stargate. If both DVNs agree on a message, it is verified and can be executed by an Executor at the destination. This configuration can be changed at any time by the StargateMultisig.
Users can be censored if any of the two whitelisted DVNs fail to approve the transaction.
Funds can be stolen if both whitelisted DVNs collude to submit a fraudulent message.
Destination Tokens
Since Stargate is mainly a Liquidity Network, its liquidity pools at the destination are filled with tokens from canonical or other bridges than Stargate. As no new tokens are minted, the users do not inherit the risk of the Stargate bridge as soon as the bridging is complete. For chains where a destination asset is not available, Stargate v2 offers a Token Bridge mode called Hydra that locks the asset at the source and mints a Stargate OFT at the destination.
Ethereum
Actors:
Is tasked to execute verified messages at the destination for a fee paid at the origin. Jobs are assigned to this contract by the LayerZero Endpoint.
- Can interact with SendUln302
- execute Stargate messages sent via LayerZero at the destination
One of the registered DVNs for the OApp acts through this smart contract. They are allowed to verify LayerZero messages for the Stargate bridge and enable their execution at the destination.
- Can interact with ReceiveUln302
- verify Stargate messages sent via LayerZero
- Can upgrade with no delay
- LayerZero Executor
One of the registered DVNs for the OApp acts through this smart contract. They are allowed to verify LayerZero messages for the Stargate bridge and enable their execution at the destination.
- Can interact with ReceiveUln302
- verify Stargate messages sent via LayerZero
A Multisig with 3/5 threshold. Custom multisignature contract allowing offchain signing and execution on multiple target chains.
- Can interact with EndpointV2
- configure the default send/receive libraries used for verification, affecting all OApps that have not set up a custom security config
- Can interact with ReadLib1002
- configure the settings of this library, affecting all OApps that have not set up a custom security config
- Can interact with SendUln302
- configure the settings of this library, affecting all OApps that have not set up a custom security config
- Can interact with ReceiveUln302
- configure the settings of this library, affecting all OApps that have not set up a custom security config
A Multisig with 3/6 threshold. Custom multisignature contract allowing offchain signing and execution on multiple target chains.
- Can interact with Treasurer
- set the admin address and withdraw treasury fees from the contract
- Can interact with StargatePool
- set critical configurations of the pool, potentially stealing funds
- withdraw fees and tokens that are not the pool token (sent by mistake) Treasurer
- Can interact with CreditMessaging
- set OApp delegate, planner and critical configurations
- Can interact with TokenMessagingEthereum
- set OApp delegate and crosschain peers, manage assets and other critical configurations
- Can interact with StargatePoolNative
- set critical configurations of the pool, potentially stealing funds
- withdraw fees and tokens that are not the pool token (sent by mistake) Treasurer
- Can interact with StargatePoolEURC
- set critical configurations of the pool, potentially stealing funds
- withdraw fees and tokens that are not the pool token (sent by mistake) Treasurer
- Can interact with StargatePoolMigratable
- set critical configurations of the pool, potentially stealing funds
- withdraw fees and tokens that are not the pool token (sent by mistake) Treasurer
- Can interact with StargatePoolUSDC
- set critical configurations of the pool, potentially stealing funds
- withdraw fees and tokens that are not the pool token (sent by mistake) Treasurer
- Can interact with StargatePool
- set critical configurations of the pool, potentially stealing funds
- withdraw fees and tokens that are not the pool token (sent by mistake) Treasurer
- Can interact with StargatePool
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with CreditMessaging
- send credits (asset claims) from pools on this chain to other pools
- Can interact with StargatePoolNative
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolEURC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolMigratable
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolUSDC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePool
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
Arbitrum One
Actors:
- Can interact with StargatePoolNative
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolMigratable
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolUSDC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
Base Chain
Actors:
- Can interact with StargatePoolUSDC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolEURC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolNative
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
Linea
Actors:
- Can interact with StargatePoolNative
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
OP Mainnet
Actors:
- Can interact with StargatePoolMigratable
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolUSDC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolNative
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
Scroll
Actors:
- Can interact with StargatePoolUSDC
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)
- Can interact with StargatePoolNative
- pause the pool and set deficit offsets (affects crosschain liquidity and fees)

Arbitrum One
A LayerZero OApp owned by Stargate that manages bridging messages from all pools on Ethereum. It can batch messages with a ‘bus’ mode or dispatch them immediately (taxi) for higher fees.
- This contract stores the following tokens: USDT.
- Roles:
- planner: EOA 1
- This contract stores the following tokens: ETH.
- Roles:
- planner: EOA 1
- This contract stores the following tokens: USDT.
- Roles:
- planner: EOA 1
- This contract stores the following tokens: USDC.
Base Chain
- Roles:
- planner: EOA 2
- This contract stores the following tokens: USDC.
A LayerZero OApp owned by Stargate that manages bridging messages from all pools on Ethereum. It can batch messages with a ‘bus’ mode or dispatch them immediately (taxi) for higher fees.
- Roles:
- planner: EOA 2
- This contract stores the following tokens: EURC.
- Roles:
- planner: EOA 2
- This contract stores the following tokens: ETH.
Ethereum
Permissions proxy allowing addresses to act through it.
- Roles:
- admin: Stargate Multisig 2
- owner: Stargate Multisig 2
A contract that is part of the LayerZero messaging protocol. The Stargate OApp owner can configure verification (MessageLib) and execution settings here.
- Roles:
- owner: LayerZero Multisig
Simple LayerZero library that blocks all messages if configured.
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
- treasurer: Treasurer; ultimately Stargate Multisig 2
- This contract stores the following tokens: mETH.
A LayerZero OApp owned by Stargate that is used for the virtual crosschain accounting of available tokens to the local pools. A local pool thus has a record of how many tokens are available when bridging to another remote pool. The permissioned Planner role can move these credits.
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
A LayerZero OApp owned by Stargate that manages bridging messages from all pools on Ethereum. It can batch messages with a ‘bus’ mode or dispatch them immediately (taxi) for higher fees.
- Roles:
- owner: Stargate Multisig 2
LayerZero library used to read state from remote blockchains.
- Roles:
- owner: LayerZero Multisig
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
- treasurer: Treasurer; ultimately Stargate Multisig 2
- This contract stores the following tokens: ETH.
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
- treasurer: Treasurer; ultimately Stargate Multisig 2
- This contract stores the following tokens: EURC.
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
- treasurer: Treasurer; ultimately Stargate Multisig 2
- This contract stores the following tokens: USDT.
Send Library used by LayerZero, defining the protocol/execution of sent messages.
- Roles:
- getExecutorConfig: LayerZero Executor
- owner: LayerZero Multisig
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
- treasurer: Treasurer; ultimately Stargate Multisig 2
- This contract stores the following tokens: USDC.
- Roles:
- owner: Stargate Multisig 2
- planner: EOA 3
- treasurer: Treasurer; ultimately Stargate Multisig 2
- This contract stores the following tokens: Metis.
Linea
A LayerZero OApp owned by Stargate that manages bridging messages from all pools on Ethereum. It can batch messages with a ‘bus’ mode or dispatch them immediately (taxi) for higher fees.
- Roles:
- planner: EOA 4
- This contract stores the following tokens: ETH.
OP Mainnet
- Roles:
- planner: EOA 5
- This contract stores the following tokens: USDT.
- Roles:
- planner: EOA 5
- This contract stores the following tokens: USDT.
- Roles:
- planner: EOA 5
- This contract stores the following tokens: USDC.
A LayerZero OApp owned by Stargate that manages bridging messages from all pools on Ethereum. It can batch messages with a ‘bus’ mode or dispatch them immediately (taxi) for higher fees.
Scroll
- Roles:
- planner: EOA 6
- This contract stores the following tokens: USDC.
A LayerZero OApp owned by Stargate that manages bridging messages from all pools on Ethereum. It can batch messages with a ‘bus’ mode or dispatch them immediately (taxi) for higher fees.
- Roles:
- planner: EOA 6
- This contract stores the following tokens: ETH.
Value Secured is calculated based on these smart contracts and tokens:
Stargate liquidity pool for EURC on Ethereum.
Stargate liquidity pool for USDC on Ethereum.
Stargate liquidity pool for ETH on Ethereum.
Stargate liquidity pool for USDT on Ethereum.
Stargate liquidity pool for METIS on Ethereum.
Stargate liquidity pool for mETH on Ethereum.
Stargate liquidity pool for USDC on Arbitrum.
Stargate liquidity pool for USDT on Arbitrum.
Stargate liquidity pool for ETH on Arbitrum.
Stargate liquidity pool for USDC on Optimism.
Stargate liquidity pool for ETH on Optimism.
Stargate liquidity pool for USDT on Optimism.
Stargate liquidity pool for EURC on Base.
Stargate liquidity pool for USDC on Base.
Stargate liquidity pool for ETH on Base.
Stargate liquidity pool for USDC on Scroll.
Stargate liquidity pool for ETH on Scroll.
Stargate liquidity pool for ETH on Linea.
The current deployment carries some associated risks:
Funds can be stolen if the OApp owner changes the configuration of the OApp to a malicious DVN.
Funds can be frozen if the permissioned Planner moves all credits away from the users' chain, preventing them from bridging.
Funds can be stolen if the source code of unverified contracts contains malicious code (CRITICAL).